Intro
Boost cybersecurity with 5 US Marines cyber tips, leveraging military-grade security strategies, threat intelligence, and online protection techniques to safeguard against cyber threats and enhance digital defense.
The importance of cybersecurity cannot be overstated, especially for individuals serving in the military, such as the US Marines. As technology advances and the world becomes increasingly digital, the risk of cyber threats and attacks also grows. It is essential for US Marines to be aware of the potential dangers and take steps to protect themselves and their sensitive information. In this article, we will discuss five cyber tips that US Marines can follow to enhance their cybersecurity and stay safe online.
Cybersecurity is a critical aspect of modern warfare, and the US Marines are at the forefront of this battle. With the rise of cyber warfare, it is more important than ever for military personnel to be knowledgeable about cybersecurity and how to protect themselves from cyber threats. By following these five cyber tips, US Marines can significantly reduce the risk of cyber attacks and protect their personal and sensitive information.
The US Marines are known for their bravery, discipline, and dedication to their country. However, even the most skilled and trained individuals can fall victim to cyber attacks if they are not aware of the potential dangers and do not take the necessary precautions. Cybersecurity is not just a matter of personal safety; it is also a matter of national security. By protecting themselves from cyber threats, US Marines can help to protect their country and its interests.
Understanding Cyber Threats
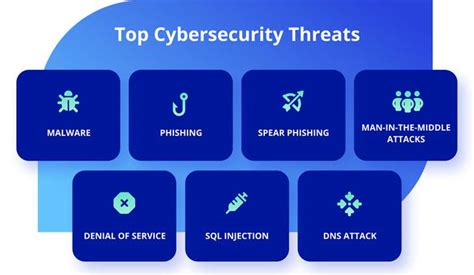
Types of Cyber Threats
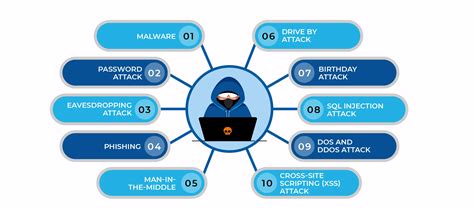
There are several types of cyber threats that US Marines should be aware of, including: * Malware: This includes viruses, worms, and trojans, which can harm or exploit a computer system. * Phishing: This involves sending fake emails or messages that appear to be from a legitimate source, with the goal of obtaining sensitive information. * Social engineering: This involves manipulating individuals into divulging sensitive information or performing certain actions. * Denial of Service (DoS) attacks: These involve overwhelming a computer system with traffic in order to make it unavailable to users. * Man-in-the-Middle (MitM) attacks: These involve intercepting communication between two parties in order to steal sensitive information.Tip 1: Use Strong Passwords

Best Practices for Passwords
Here are some best practices for passwords that US Marines should follow: * Use a password manager to generate and store unique, complex passwords. * Avoid using easily guessable information, such as names or birthdates. * Do not use the same password for multiple accounts. * Change passwords regularly, ideally every 60-90 days. * Use two-factor authentication (2FA) whenever possible.Tip 2: Keep Software Up-to-Date

Importance of Software Updates
Software updates are essential for protecting against cyber threats because they: * Patch security vulnerabilities, which can help to prevent cyber attacks. * Improve performance and stability. * Add new features and functionality. * Enhance user experience.Tip 3: Be Cautious with Emails and Attachments

Best Practices for Email Safety
Here are some best practices for email safety that US Marines should follow: * Avoid opening emails or attachments from unknown sources. * Be wary of emails that ask for sensitive information or contain suspicious links. * Use spam filters and antivirus software to scan emails and attachments. * Avoid using public computers or public Wi-Fi to access sensitive information.Tip 4: Use Encryption
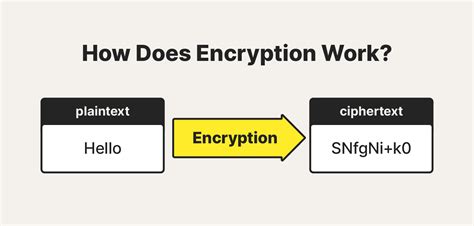
Types of Encryption
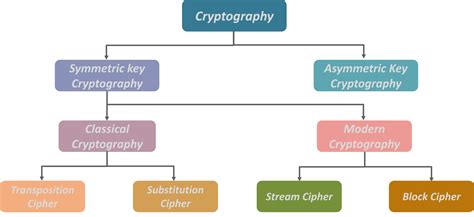
There are several types of encryption that US Marines can use, including: * Symmetric encryption: This involves using the same key for both encryption and decryption. * Asymmetric encryption: This involves using a pair of keys, one for encryption and one for decryption. * Hashing: This involves using a one-way algorithm to convert plaintext into a fixed-length string of characters.Tip 5: Monitor Accounts and Credit Reports

Importance of Monitoring Accounts
Monitoring accounts and credit reports is essential for protecting against identity theft and financial fraud because it: * Helps to detect suspicious activity early on. * Prevents financial loss and damage to credit scores. * Allows individuals to take action quickly to prevent further damage.Cybersecurity Image Gallery







What is the most common type of cyber threat?
+The most common type of cyber threat is phishing, which involves sending fake emails or messages that appear to be from a legitimate source.
How can I protect myself from malware?
+You can protect yourself from malware by using antivirus software, avoiding suspicious links and attachments, and keeping your software up-to-date.
What is two-factor authentication?
+Two-factor authentication is a security process that requires two forms of verification, such as a password and a code sent to your phone, to access an account or system.
How often should I change my passwords?
+You should change your passwords every 60-90 days, or whenever you suspect that your account has been compromised.
What is encryption and how does it work?
+Encryption is the process of converting plaintext into unreadable ciphertext, which can only be decrypted with the correct key or password. It works by using algorithms to scramble the data, making it unreadable to unauthorized parties.
By following these five cyber tips, US Marines can significantly enhance their cybersecurity and protect themselves from cyber threats. Remember to stay vigilant and always be cautious when online, as cybersecurity is an ongoing process that requires constant attention and effort. If you have any questions or concerns about cybersecurity, feel free to comment below or share this article with others to help spread awareness about the importance of cybersecurity.
