Intro
Discover the challenges of cyber security, including complex threats, data breaches, and network vulnerabilities, making it hard to protect against cyber attacks and maintain online safety and security measures.
Cyber security has become an essential aspect of our daily lives, as we increasingly rely on technology and the internet to store and manage our personal and professional information. However, cyber security is a complex and challenging field that requires constant attention and innovation to stay ahead of emerging threats. In this article, we will explore five ways cyber security is hard, highlighting the difficulties and complexities that cyber security professionals face in protecting our digital assets.
The importance of cyber security cannot be overstated, as the consequences of a security breach can be severe and long-lasting. From financial loss to reputational damage, the impact of a cyber attack can be devastating for individuals, businesses, and organizations. Therefore, it is crucial that we understand the challenges faced by cyber security professionals and the measures they take to mitigate these risks. By recognizing the difficulties of cyber security, we can better appreciate the importance of this field and the need for continued investment and innovation.
As technology advances and becomes more sophisticated, so do the threats we face in the cyber world. Cyber attackers are constantly evolving their tactics and techniques, using new and innovative methods to bypass security measures and gain unauthorized access to sensitive information. This cat-and-mouse game between cyber security professionals and attackers makes it challenging to stay ahead of emerging threats and protect our digital assets. Furthermore, the increasing complexity of technology and the interconnectedness of our devices and systems create new vulnerabilities and risks that must be addressed.
Complexity of Cyber Threats
The complexity of cyber threats is further exacerbated by the increasing use of cloud computing, mobile devices, and the Internet of Things (IoT). These technologies create new vulnerabilities and risks that must be addressed, as they often involve multiple devices, systems, and networks that must be secured. Moreover, the lack of standardization and regulation in these areas creates challenges for cyber security professionals, who must navigate a complex landscape of technologies and threats to protect our digital assets.
Types of Cyber Threats
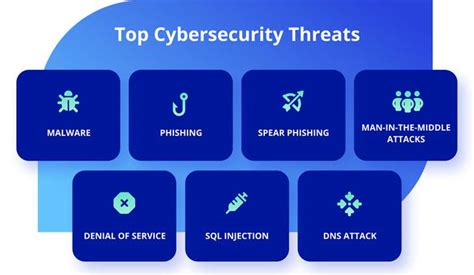
Some common types of cyber threats include: * Malware: software designed to harm or exploit a computer system * Phishing: a type of social engineering attack that uses email or other communication to trick users into revealing sensitive information * Ransomware: a type of malware that encrypts a victim's files and demands payment in exchange for the decryption key * Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks: attacks that overwhelm a system or network with traffic in order to make it unavailable to usersLack of Skilled Cyber Security Professionals

The lack of skilled cyber security professionals is also exacerbated by the rapidly evolving nature of cyber threats. As new threats emerge, cyber security professionals must continually update their skills and knowledge to stay ahead of the threats. This requires significant investment in training and education, as well as a commitment to ongoing learning and professional development. Moreover, the high stress and pressure of working in cyber security can lead to burnout and turnover, further exacerbating the shortage of skilled professionals.
Ways to Address the Shortage of Skilled Cyber Security Professionals
Some ways to address the shortage of skilled cyber security professionals include: * Investing in education and training programs that focus on cyber security * Providing opportunities for career development and advancement in the field * Encouraging diversity and inclusion in the cyber security industry * Offering competitive salaries and benefits to attract and retain top talentIncreasing Sophistication of Attackers

The increasing sophistication of attackers is also driven by the growing availability of cyber crime tools and services on the dark web. These tools and services, such as malware and distributed denial-of-service (DDoS) attacks, can be purchased and used by attackers with relatively little technical expertise. This has democratized cyber crime, allowing a wider range of individuals and groups to launch attacks and exploit vulnerabilities.
Ways to Combat Sophisticated Attackers
Some ways to combat sophisticated attackers include: * Implementing advanced security measures, such as artificial intelligence and machine learning-based detection systems * Conducting regular security audits and vulnerability assessments to identify and address weaknesses * Providing education and training to users on how to identify and avoid social engineering attacks * Encouraging a culture of security awareness and vigilance within organizationsEvolution of Technology and Infrastructure

The evolution of technology and infrastructure is also driven by the growing demand for greater connectivity and convenience. This has led to the development of new technologies and infrastructure, such as 5G networks and smart cities, which create new opportunities for cyber attackers to exploit. Moreover, the lack of standardization and regulation in these areas creates challenges for cyber security professionals, who must navigate a complex landscape of technologies and threats to protect our digital assets.
Ways to Address the Evolution of Technology and Infrastructure
Some ways to address the evolution of technology and infrastructure include: * Implementing security measures that are designed to adapt to evolving technologies and infrastructure * Conducting regular security audits and vulnerability assessments to identify and address weaknesses * Providing education and training to users on how to securely use new technologies and infrastructure * Encouraging a culture of security awareness and vigilance within organizationsHuman Factor in Cyber Security

The human factor is also driven by the growing demand for greater convenience and usability. This has led to the development of new technologies and infrastructure, such as password managers and single sign-on solutions, which create new opportunities for cyber attackers to exploit. Moreover, the lack of awareness and education among users creates challenges for cyber security professionals, who must navigate a complex landscape of human behavior and psychology to protect our digital assets.
Ways to Address the Human Factor in Cyber Security
Some ways to address the human factor in cyber security include: * Providing education and training to users on how to securely use technology and infrastructure * Implementing security measures that are designed to adapt to human behavior and psychology * Encouraging a culture of security awareness and vigilance within organizations * Conducting regular security audits and vulnerability assessments to identify and address weaknessesCyber Security Image Gallery








What is the most significant challenge facing the cyber security industry?
+The most significant challenge facing the cyber security industry is the increasing sophistication of attackers, who are using advanced technologies and tactics to launch complex and effective attacks.
How can organizations address the shortage of skilled cyber security professionals?
+Organizations can address the shortage of skilled cyber security professionals by investing in education and training programs, providing opportunities for career development and advancement, and offering competitive salaries and benefits to attract and retain top talent.
What is the most effective way to combat sophisticated attackers?
+The most effective way to combat sophisticated attackers is to implement advanced security measures, such as artificial intelligence and machine learning-based detection systems, and to conduct regular security audits and vulnerability assessments to identify and address weaknesses.
How can users protect themselves from cyber attacks?
+Users can protect themselves from cyber attacks by being aware of the risks and taking steps to mitigate them, such as using strong passwords, keeping software up to date, and being cautious when clicking on links or opening attachments from unknown sources.
What is the importance of cyber security awareness and training?
+Cyber security awareness and training are essential for protecting our digital assets and preventing cyber attacks. By educating users on how to securely use technology and infrastructure, organizations can reduce the risk of cyber attacks and protect their sensitive information.
In final thoughts, the challenges facing the cyber security industry are significant and complex. From the increasing sophistication of attackers to the shortage of skilled cyber security professionals, there are many obstacles that must be overcome to protect our digital assets. However, by understanding these challenges and taking steps to address them, we can reduce the risk of cyber attacks and create a safer and more secure digital environment. We invite you to share your thoughts and experiences on this topic, and to take action to protect yourself and your organization from cyber threats. By working together, we can create a more secure and resilient digital world.

