Intro
Discover the 5 key differences, highlighting crucial distinctions, comparisons, and contrasts, to make informed decisions with expert analysis and insights.
The world of technology is constantly evolving, and with it, the ways in which we interact with devices and systems. One of the most significant advancements in recent years has been the development of various technologies that have changed the way we live, work, and communicate. Understanding the differences between these technologies is crucial for making informed decisions and staying ahead of the curve. In this article, we will explore the 5 key differences between some of the most popular technologies, highlighting their unique features, benefits, and applications.
The importance of understanding these differences cannot be overstated. As technology continues to advance at a rapid pace, it can be overwhelming to keep up with the latest developments. By grasping the fundamental differences between these technologies, individuals and organizations can make informed decisions about which solutions best meet their needs. Whether you're a tech enthusiast, a business leader, or simply someone looking to stay up-to-date with the latest trends, this article is designed to provide valuable insights and practical information.
The 5 key differences we will be exploring are critical in understanding the nuances of each technology. From their underlying architectures to their applications and use cases, each technology has its own strengths and weaknesses. By examining these differences, we can gain a deeper understanding of how these technologies can be leveraged to drive innovation, improve efficiency, and solve real-world problems. Whether you're looking to improve your personal productivity, drive business growth, or simply stay ahead of the curve, this article is designed to provide the information and insights you need to succeed.
Introduction to Key Technologies
In order to understand the 5 key differences, it's essential to have a basic understanding of the technologies involved. Each technology has its own unique history, development, and application. By exploring these technologies in more depth, we can gain a better understanding of their strengths and weaknesses, as well as their potential applications. From artificial intelligence to the Internet of Things, each technology has its own distinct characteristics and use cases.
Technology 1: Artificial Intelligence
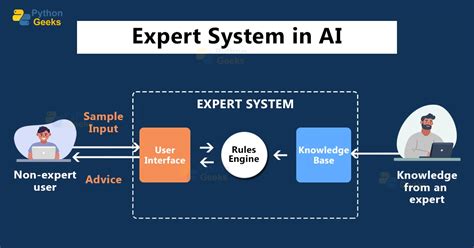
Artificial intelligence (AI) refers to the development of computer systems that can perform tasks that would typically require human intelligence. This includes tasks such as learning, problem-solving, and decision-making. AI has a wide range of applications, from virtual assistants to self-driving cars. By leveraging AI, organizations can automate routine tasks, improve efficiency, and drive innovation.
Key Features of Artificial Intelligence
Some of the key features of AI include: * Machine learning: the ability of systems to learn from data and improve their performance over time * Natural language processing: the ability of systems to understand and generate human language * Computer vision: the ability of systems to interpret and understand visual data * Expert systems: the ability of systems to mimic the decision-making abilities of a human expertTechnology 2: Internet of Things

The Internet of Things (IoT) refers to the network of physical devices, vehicles, and other items that are embedded with sensors, software, and connectivity, allowing them to collect and exchange data. This includes devices such as smart home appliances, wearable fitness trackers, and autonomous vehicles. By leveraging IoT, organizations can improve efficiency, reduce costs, and drive innovation.
Key Features of Internet of Things
Some of the key features of IoT include: * Connectivity: the ability of devices to connect to the internet and exchange data * Sensors: the ability of devices to collect and transmit data * Automation: the ability of devices to perform tasks automatically * Analytics: the ability of devices to analyze data and provide insightsTechnology 3: Blockchain

Blockchain refers to a decentralized, digital ledger that records transactions across a network of computers. This includes transactions such as cryptocurrency exchanges, supply chain management, and voting systems. By leveraging blockchain, organizations can improve security, reduce costs, and increase transparency.
Key Features of Blockchain
Some of the key features of blockchain include: * Decentralization: the ability of the ledger to be maintained by a network of computers * Security: the ability of the ledger to be secure and resistant to tampering * Transparency: the ability of the ledger to provide a clear and transparent record of transactions * Immutability: the ability of the ledger to be immutable and resistant to alterationTechnology 4: Cloud Computing

Cloud computing refers to the delivery of computing services over the internet, such as storage, processing power, and software applications. This includes services such as Amazon Web Services, Microsoft Azure, and Google Cloud Platform. By leveraging cloud computing, organizations can improve scalability, reduce costs, and increase flexibility.
Key Features of Cloud Computing
Some of the key features of cloud computing include: * Scalability: the ability of services to scale up or down to meet changing demands * Flexibility: the ability of services to be accessed from anywhere and on any device * Cost-effectiveness: the ability of services to reduce costs and improve efficiency * Reliability: the ability of services to provide high levels of uptime and availabilityTechnology 5: Cybersecurity

Cybersecurity refers to the practices and technologies designed to protect digital information and systems from cyber threats, such as hacking, malware, and phishing. This includes measures such as firewalls, antivirus software, and encryption. By leveraging cybersecurity, organizations can protect their data, prevent cyber attacks, and maintain customer trust.
Key Features of Cybersecurity
Some of the key features of cybersecurity include: * Threat detection: the ability to detect and identify potential cyber threats * Incident response: the ability to respond quickly and effectively to cyber attacks * Vulnerability management: the ability to identify and remediate vulnerabilities in systems and applications * Compliance: the ability to meet regulatory requirements and industry standards5 Key Differences Image Gallery



What are the 5 key differences between these technologies?
+The 5 key differences between these technologies are their underlying architectures, applications, use cases, benefits, and challenges. Each technology has its own unique features, advantages, and disadvantages, and understanding these differences is essential for making informed decisions.
How do these technologies impact business and society?
+These technologies have a significant impact on business and society, driving innovation, improving efficiency, and transforming the way we live and work. They also raise important questions about ethics, privacy, and security, and it's essential to consider these implications when adopting and implementing these technologies.
What are the benefits and challenges of each technology?
+Each technology has its own benefits and challenges. For example, artificial intelligence can improve efficiency and drive innovation, but it also raises concerns about job displacement and bias. Blockchain can improve security and transparency, but it also faces challenges related to scalability and regulation. Understanding these benefits and challenges is essential for making informed decisions and maximizing the potential of these technologies.
In conclusion, the 5 key differences between these technologies are critical in understanding their unique features, benefits, and applications. By leveraging these technologies, organizations can drive innovation, improve efficiency, and solve real-world problems. However, it's also essential to consider the challenges and implications of these technologies, and to make informed decisions about which solutions best meet their needs. We hope this article has provided valuable insights and practical information, and we encourage readers to continue exploring and learning about these exciting and rapidly evolving technologies.
